A new wave of cyberattacks has targeted users across Europe, with DroidBot, an advanced Android Remote Access Trojan (RAT), quickly becoming one of the most dangerous threats to UK banking and cryptocurrency apps. Operating as Malware-as-a-Service (MaaS), DroidBot allows cybercriminals to access sensitive financial information, hijack devices, and execute sophisticated attacks, all with minimal technical expertise.
What is DroidBot and How Does It Work?
DroidBot is a highly advanced Remote Access Trojan (RAT) that operates on a Malware-as-a-Service model. For a monthly fee of just $3,000, cybercriminals gain access to everything they need to conduct a full-scale attack: a malware builder, command-and-control (C2) servers, and an admin panel to manage operations.
Once installed, DroidBot grants attackers total control over the victim’s device, enabling them to intercept SMS messages, log keystrokes, and perform overlay attacks on banking and crypto apps. It’s these capabilities that make DroidBot particularly dangerous to anyone using UK financial apps such as HSBC, Barclays, and NatWest.
Some key functions of DroidBot include:
- SMS Interception: Hijacking SMS codes used for two-factor authentication (2FA), allowing cybercriminals to bypass security checks.
- Keylogging: Capturing login credentials, personal details, and other sensitive information as users type.
- Overlay Attacks: Displaying fake login pages on top of legitimate banking apps to steal account credentials.
- Remote Device Control: Giving attackers full control over infected devices, enabling them to execute actions as if they were physically holding the phone.
This combination of features makes DroidBot an exceptionally potent weapon in the hands of cybercriminals targeting UK banking customers and cryptocurrency investors.
DroidBot’s Expanding Reach: UK on High Alert
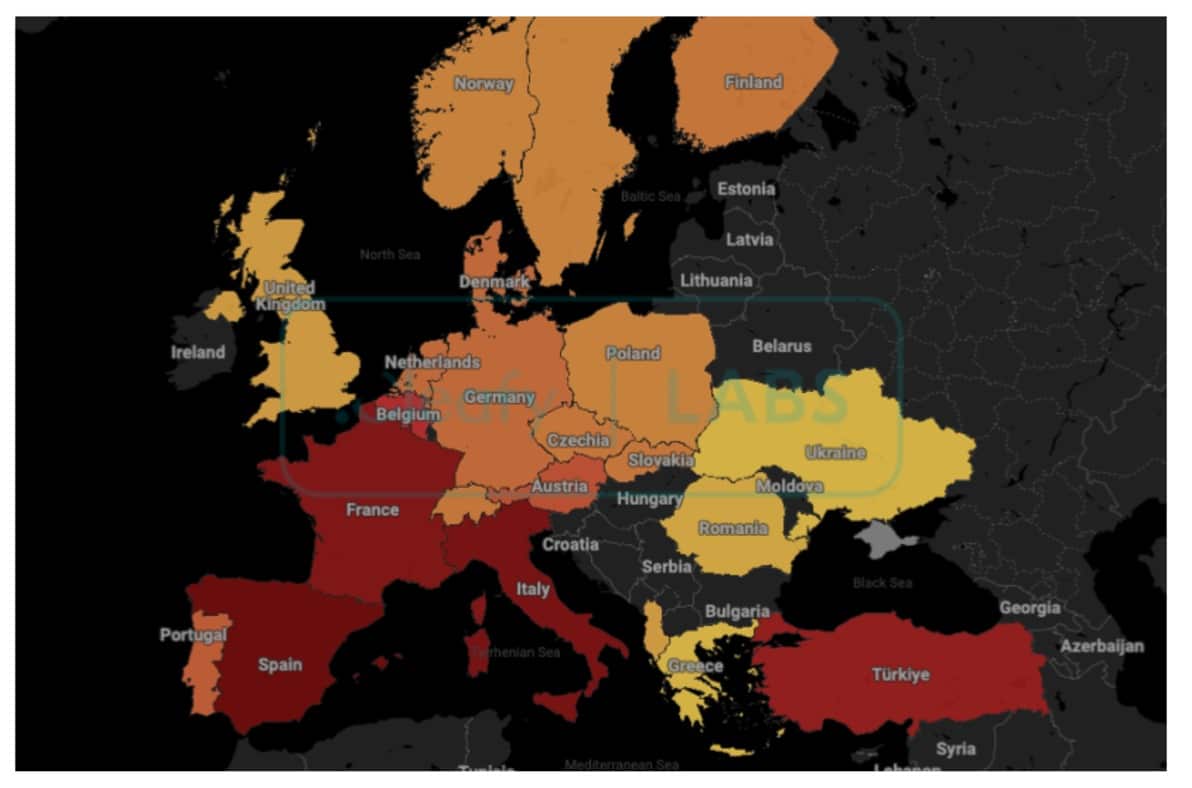
Since its discovery in October 2024, DroidBot has spread rapidly, with infections reported in several European countries, including France, Italy, and Spain. But it’s the UK that has emerged as a particular hotspot for DroidBot attacks. Cleafy researchers have identified over 770 infections across the continent, with many victims hailing from major UK cities, including London, Manchester, and Birmingham.
Financial institutions in the UK are under increasing threat, with various high-profile banking apps falling victim to DroidBot. Among the targeted apps are:
- HSBC
- Barclays
- NatWest
- Santander UK
- Lloyds Banking Group
- Monzo
- Revolut
According to Cleafy, the malware is also targeting popular crypto apps such as Binance, Kraken, and Metamask, which are widely used by UK investors. These apps provide an attractive target for cybercriminals looking to steal funds from users with significant cryptocurrency holdings.
A Network of Malicious Affiliates
- 17 cybercriminal groups have been identified using DroidBot to conduct their attacks, including numerous with ties to the UK.
- Infections have been most prominent in France, Belgium, Spain, and Italy, but UK-based banks and financial services are now particularly vulnerable.
- Researchers suggest the Malware-as-a-Service (MaaS) model used by DroidBot is helping low-skill hackers carry out large-scale attacks against UK banks and financial institutions.
These findings highlight the growing sophistication of cybercrime networks targeting the UK, using DroidBot as their weapon of choice. The following table represents a summary of the TTP behind DroidBot campaigns:
The MaaS Model: Profiting from DroidBot
What makes DroidBot particularly dangerous is its Malware-as-a-Service model. This enables even less experienced cybercriminals to launch highly effective attacks without needing deep technical expertise. For just $3,000 per month, attackers can access the entire DroidBot infrastructure, including malware-building tools, C2 servers, and a centralized admin panel to track stolen data and control infected devices.
The MaaS model offers several features that make DroidBot so effective:
- Customizable Malware Builder: Attackers can modify the malware to tailor it to specific targets, such as UK-based banking or crypto apps.
- Command-and-Control Servers: These servers enable real-time communication between the attacker and the infected devices.
- Admin Panel: Allows cybercriminals to manage their operations, extract stolen data, and issue commands remotely.
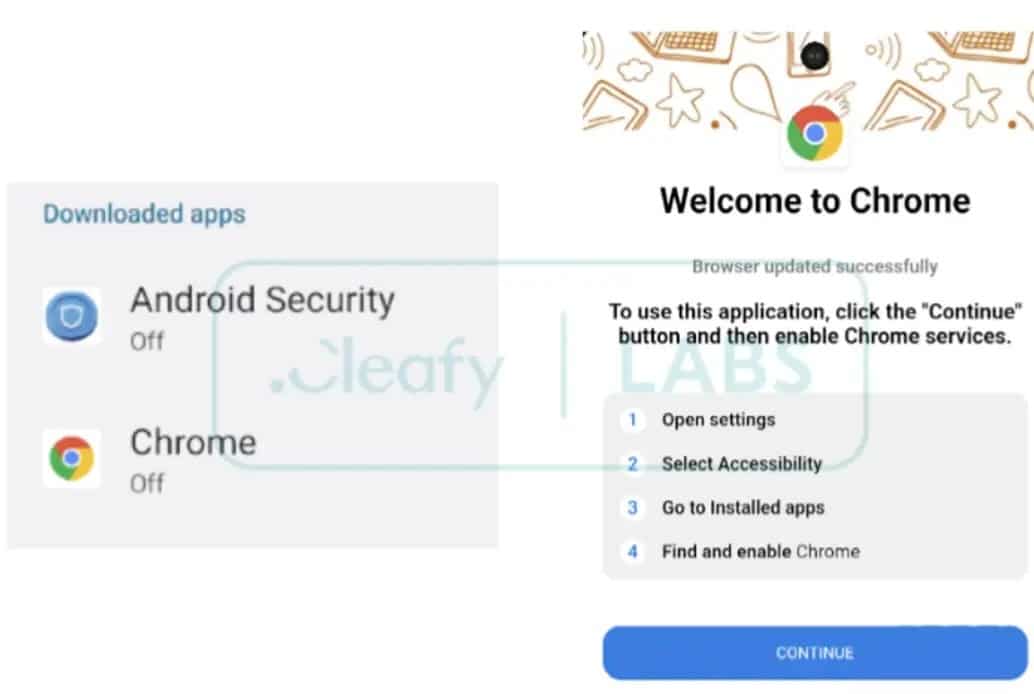
- Deceptive Tactics: DroidBot is designed to look like legitimate apps or services (e.g., fake Google services or banking apps) to trick users into installing it.
This ease of use and access has made DroidBot a popular choice among cybercriminals targeting financial institutions, including banks in the UK.
What Makes DroidBot So Dangerous?
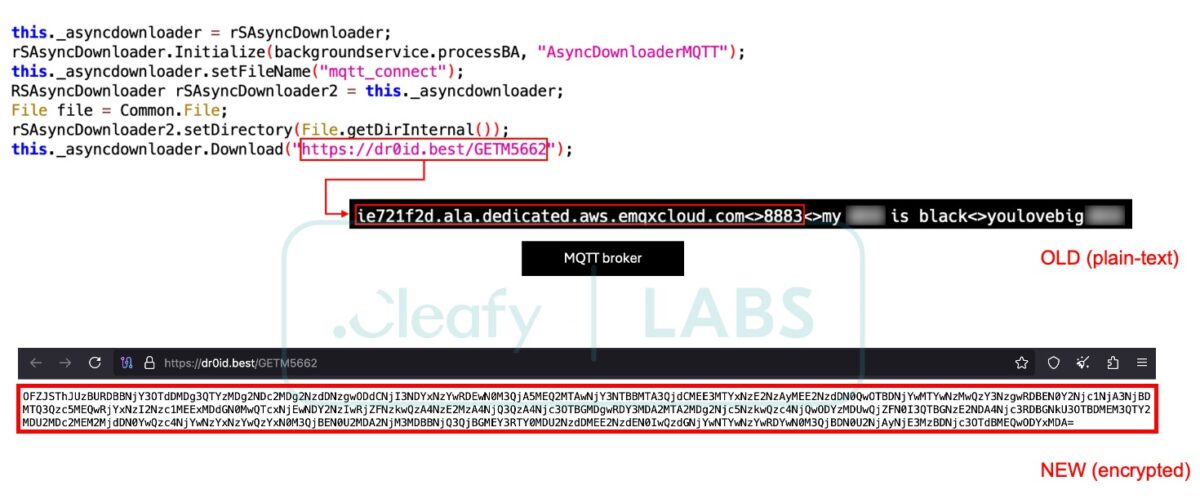
DroidBot’s ability to bypass traditional security measures is one of its most dangerous features. Using a dual-channel communication system, DroidBot separates inbound commands (sent via HTTPS) from outbound data, which is transmitted via MQTT. This separation enhances its resilience and flexibility, making it more difficult for security tools to detect and block it.
Moreover, DroidBot’s use of Android’s Accessibility Services gives it full control over an infected device. Researchers at Cleafy noted that DroidBot can carry out remote surveillance, keylogging, and SMS interception, further compromising the device’s security.
How to Protect Yourself from DroidBot
To protect against DroidBot, users, particularly those using UK banking and financial apps, must be vigilant and take proactive steps:
- Download Apps from Trusted Sources: Stick to the Google Play Store for app downloads and avoid third-party platforms, which are often sources of malicious software.
- Review App Permissions: Carefully check the permissions that apps request, especially Accessibility Services, and avoid granting unnecessary access.
- Activate Play Protect: Make sure Google Play Protect is enabled to detect and remove malicious apps.
- Use Stronger Authentication: Where possible, avoid relying solely on SMS for two-factor authentication. Use a more secure method such as Google Authenticator or Authy.
The Growing Threat of DroidBot in the UK
With UK-based banks and financial services continuing to be targeted, experts warn that the full scale of the DroidBot threat has yet to be realized. As the malware spreads, its ability to bypass traditional security measures will only increase, leaving both consumers and businesses vulnerable to devastating attacks.